Network Security
Vulnerability Scanning (VulScan)
Tips/Info
The best way to get a grip over the cost of a data breach is by finding out how the breach happened. Before you start improvising your cyber defenses, why not find out what can harm your organization the most?
Contact us for a free eBook on this topic.
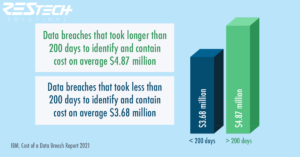
The more days you spend tracking down a data breach, the more impact it will have on your business. Most companies fail to identify why breaches happen.
How would you shield your business in this situation?
Contact us for a free eBook on this topic.
If you are responsible for IT security, you must be proactive in resolving vulnerabilities. What’s stopping you?
Need help preparing and executing a vulnerability defense strategy?
Contact us for a free eBook on this topic.
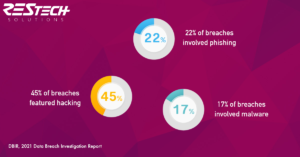
A data breach could destroy your brand reputation and hurt your ROI significantly. Do you know the most common type of data breaches today and how they could impact your business?
Request an eBook to learn more.
Do emails that seem genuine but contain malicious links end up in your inbox? Your employees might fall prey to these tricks and disclose sensitive data.
You need an advanced security solution that will protect your organization against phishing emails.
What are you doing to help your employees spot these scams?
Downtime is the most exorbitant part of experiencing a ransomware attack. It may cost businesses 10X of the ransom.
Strengthen your backup systems to ensure automated application recovery and business continuity.
Contact us to request an eBook on this topic.
Your clients expect you to ensure the confidentiality and security of their sensitive data. What happens if you don’t?
They will simply turn to your competitors.
Contact us to find out how you can strengthen your cybersecurity to drive growth.
Assessing vulnerabilities and applying patches in real-time to business applications is critical to ensuring systems security. With vulnerability scanners, you can be on top of missing patches in your business environment in real time.
Contact us to request an eBook on this topic.
Most SMBs lack skilled resources to manage the multitude of threats that are popping up every day. They are clueless how to spot and contain ransomware with vulnerability scanning.
Have you been struggling with the same? You need a partner who will take care of it for you.
Contact us to get an eBook on this topic.