Data Security
January 2022 - Refresh
Tips/Info
It’s not IF but WHEN your organization suffers a data breach. Ask us how you can proactively protect customer and employee PII.
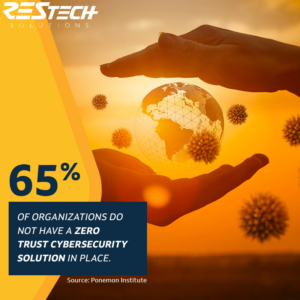
Only 20% of organizations have fully implemented the zero trust cybersecurity model that reduces incident costs. Contact us to see if this technology makes sense for your organization.
While it’s nice to share, treat your passwords like your toothbrush – and don’t share them with anyone, don’t leave them exposed, and DO change them regularly.
Better yet– consider investing in 2-Factor Authentication for a higher level of security. Don’t let a brute force password hacker cause damage to your business!
With cyberattacks on the rise, organizations can catch breaches and potential threats faster with the help of cybersecurity solutions using AI automation. Contact us to learn more.
Without the proper training, remote workers tend to overestimate their knowledge of cybersecurity basics. Talk to us today to learn how your employees can become your strongest defense.
When was the last time your business reviewed its security measures? When it comes to cybersecurity, having a set-it-and-forget-it mentality is increasingly dangerous. Contact us today to learn how we can get your response plan updated.
Reduce remote work security risks and costs. Contact us to learn how we can help you proactively look for and close remote work security gaps.
Discover the core elements of information security. To audit or implement these principles in your organization, contact us for details.