Remote Workforce
January 2021 - Backup
Tips/Info
If there is one positive result of forcing a total quarantine shut down of businesses worldwide, it is that organizations can understand and verify the power and functionality of a digital transformation.
Organizations can now explore new and untapped opportunities they had not previously considered possible; however, it is crucial that businesses assess, monitor, and re-enforce the proper security controls, policies, and procedures that have been adapted to include total or partial decentralized work environments with remote users.
The digital age is well established and becoming part of the foundation of how the world creates, utilizes, and stores data. Much of the data created in recent years and into the future will only have a digital footprint. It will be imperative that individuals and businesses alike make accommodations, plans, and systems to ensure that the integrity and availability of this data are protected long-term.
For most businesses, data is crucial to performing normal operations and would be irreplaceable if ever corrupted or lost completely. The consequences and costs of a major security or data loss incident would be a disaster and even imagining the possible outcomes triggers nightmares.
Is your organization taking its IT Security and Data Protection responsibilities seriously? You know and understand how easy and devasting a mistake or failure could be – so why would you gamble it all on mediocre tools and a conceptual response outline that will breed chaos and frustration during a crisis?
When your data is your most valuable asset, your protection strategy should never be to settle for “good enough.”
Hardware failure is inevitable. Combined with the human factor, data loss is a very real risk your organization needs to take seriously. The future is unpredictable; natural disasters can happen with little warning and with the surge in cyberattacks over the last few years, a good backup and disaster recovery plan will help you ensure your data is protected and recoverable.
Cloud storage is essentially the process of saving and housing your data on an internet-based platform instead of your local physical device. It can also be utilized to host some of your software applications and databases where you document or provide services.
In today’s world, it is not uncommon to create or accumulate vast quantities of digital records and information.
Cloud storage solves a few key problems:
✓ Running out of usable storage space on physical devices
✓ Addressing data protection and management
✓ Enabling and increasing the necessary accessibility needed for remote employees to access data securely from anywhere
In the words of Steven Covey “Begin with the end in mind.”
The success of a data recovery incident will go much smoother if you design your backup plans with the realization that you will be utilizing this plan at some point to recover and restore your data. With that said, it will be important to take time to thoroughly plan and prepare all the actions and steps your business will follow to enact your data recovery plan.
To help you get started, here are some tips for ensuring a successful data recovery and restoration process with minimum hassle.
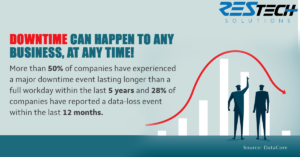
Businesses around the world have become increasingly dependent on digital technology and data to generate revenue and provide support to their customers. However, disruptive events ranging from hardware or software failures, natural disasters, human error and mistakes, and even cyberattacks can happen to any business at any time and result in costly downtime or data loss.
What tools and systems are you using to ensure that your organization can proactively avoid most disruptions? What are you using to quickly remediate, recover and resume normal operations following a data loss or downtime incident?
Surging cyberthreats and security risks have businesses of all sizes and industries on edge. Organizations that heavily rely on mission-critical data to perform or deliver their daily operations need to not only focus on protecting the actual data itself, but also implementing comprehensive business continuity and disaster recovery systems that provide crucial resiliency.
How much data loss can your business handle to survive? How long can you go without access to or utilization of that data before the costs become catastrophic?
There are a lot of threats and disasters that could wipe out your valuable data. Let us show you how a BCDR solution can provide peace of mind.
Downtime is a real and valid threat that can, and very likely will happen to all businesses at some point in time. Corrupted or lost data can cause downtime – or be the devasting result you are left with in the wake of a major downtime incident.
Neglecting to implement the proper systems or take appropriate actions to prepare, mitigate and recover from a highly probable occurrence is a foolish and dangerous way to manage your business.
Data loss is a guarantee without proper secure backup procedures and tools. There are a vast number of causes and threats which could result in data loss or corruption, the majority of which can happen in the blink of an eye or be triggered by the smallest mistake.
If any of your organization’s data and information assets are crucial to conducting normal business operations, then protecting its integrity, availability, and confidentiality with a robust and secure backup solution is a necessity.