Tips/Info
With insider threats so difficult to detect, maintaining compliance is an even more challenging task. With the ever-changing data protection regulations & cybersecurity frameworks put in place by various governing agencies worldwide, preventing insider incidents is increasingly critical to your security posture. Consider partnering with a specialist.
No one wants to make the call to their customers that their private and legally protected data has been compromised. This could not only cause irreparable damage to your customers’ trust and loyalty but could also lead to regulatory penalties and costly litigation. Make sure you are considering your legal obligations and requirements with respect to data protection, privacy, and increasing insider security threats.
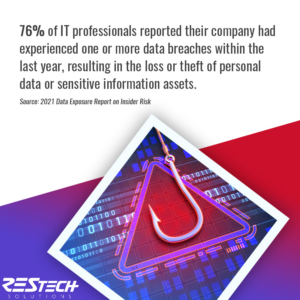
The first step to securing your business is assessing what your current security posture is and where you are falling short. This is especially important if your organization collects, processes, or stores personally identifiable information (PII) or sensitive and classified information. Not only could a breach compromise a businesses’ reputation, it can also land you in trouble with laws or regulatory requirements – resulting in huge fines.
While remote employees were an increasing part of business operations over the last few years, the number of businesses now relying on decentralized environments and remote workers has exponentially increased. In turn, this also means an increase in IT and data security risks and vulnerabilities facing organizations worldwide. Getting your business compliant is a vital step toward staving off the hackers looking for an easy payday.
Despite all the measures IT Pros take to secure a business, nothing is foolproof and there are still data breaches. People reuse passwords, respond to phishing emails, and make mistakes. That is why it is so important to have strict security controls and access permissions to not only keep your business secure but maintain data protection compliance.
Human error is a serious challenge to data security. Depending on the severity, a data breach involving sensitive or protected information can sink a business. It can be as easy as adding the wrong recipient to an email address by mistake or a user getting looped in on data or information that has nothing to do with their job responsibilities.
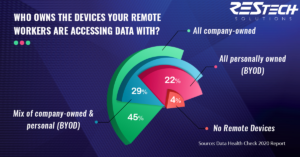
Does your business let employees use personal devices for remote work? If your business also has data protection obligations under any regulatory laws or mandates, you need to think twice about your personal or bring-your-own-device (BYOD) policies. These devices are often impossible to monitor and secure from insider attacks or cybercriminals.
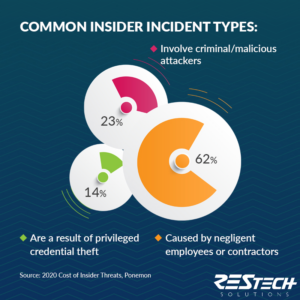
Insider incidents can have a few different types of intents or origins, but the costs and consequences are all equally damaging. Do you have the proper security controls to identify and detect common indicators or anomalous activities before they become bigger problems? Are you training your users on the required security and compliance measures needed to mitigate data breaches or exposure and protect your business-critical data?