Tips/Info
As more employees are being sent home due to the pandemic, businesses need to think about their cybersecurity from a remote standpoint. Employees around the world may not have access to business headquarters for assistance, so remote monitoring and IT management are pivotal to keep everything running smoothly.
When it comes to protecting your business, do you have strict policies and tools that allow you to control and manage who is accessing your systems and private/sensitive data?
Are you regularly educating and training your employees on proper security protocols?
Do you have the best practices necessary to identify and avoid the common mistakes or threats that could result in a security or data loss incident?
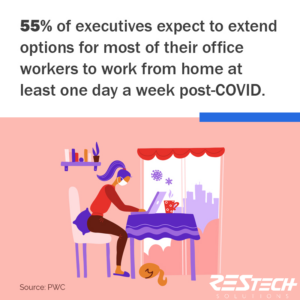
Although the pandemic doesn’t seem to be ending any time soon, organizations are already considering the potential pros and cons of incorporating or adopting remote working environments in a more long-term or even permanent operational process.
Is your business making plans for expanding its remote workforce options going forward? If so, it’s important to review and audit all operational tools, systems, and procedures to ensure that all security and compliance requirements are accounted for and maintained at every level for every user.
Cybercriminals are exploiting and taking advantage of stressed and overwhelmed employees who are trying to process their feelings about the COVID-19 virus. These employees are also navigating and adjusting to the many challenges and distractions of working from their home environments.
Failure to regularly educate and train your employees on the security protocols they need to spot and avoid dangerous cyberthreats is leaving your organization exposed to potentially catastrophic security risks.
With all the chaos experienced worldwide over the last year, implementing and maintaining strong IT security and data protection controls will help you proactively prevent or mitigate the cost and consequences that could result from unplanned downtime and costly data loss incidents.
Here are 9 essential security controls and strategies you should have in place if you are relying on a remote workforce.
Concerned about your work-from-home transition? You’re not alone. Businesses of all sizes and industries have expressed concerns that decentralized work environments and remote users hurt their security posture.
Working from home doesn’t have to mean that your organization becomes more vulnerable to cyberattacks. Contact us today to strengthen your remote security and keep your business up and running.
“Use of personal devices creates problems around document preservation matters and add increased risk. In addition, the software powering some home equipment can be months or even years out of date.” (Brenda R. Sharton, Harvard Business Review)
Although a computer may seem to function perfectly fine, old software that is out-of-date is more susceptible to cyberattacks, system failures, and hacking. Software updates include bug fixes and security measures that would resolve or eliminate newly discovered exploits or security gaps. Make sure any devices with access to business systems or data are protected with the latest security patches.
When a user must regularly access a large number of systems and applications to perform their job duties, they can quickly get overwhelmed and frustrated trying to manage all the different account passwords generated for each application.
This often results in the user ignoring rules or cutting corners, consequentially making the business network or other systems vulnerable to cyberattacks should that user’s credentials be compromised or stolen.
Most routers have a ‘default’ password that is built-in by the manufacture and will expose you to a variety of privacy risks and cyber security threats. The default logins and settings, for common devices like routers, are often well-known or easily obtained with a simple Google search.
If you do not change default login passwords, it makes it extremely easy for a malicious hacker – or even just a nosey neighbor – to gain access to your network as well as any devices, files, or data that are connected to that network.