Cyber Supply Chain Risk Management
March 2021 - Backup
Tips/Info
It’s not an exaggeration by any means to point out that most humans that access or utilize the internet have received some form of malware via a compromised email or website. With the main point of entry for malware being email, you should be extra alert with any emails coming from your supply chain. When the odds are not in your favor, you should invest in proactive data protection with a robust and multi-layered backup strategy.
Email is a prime attack method for bad actors looking to corrupt or encrypt an organization’s network and demand a ransom or extort some sort of financial gain. This has become an increasingly challenging issue along the cyber supply chain. Don’t get caught by surprise with an attack where you are blackmailed or exploited by a malicious criminal hacker. If you are ever in a situation where a hacker is attempting to extort your organization, having a backup solution in place can save your business.
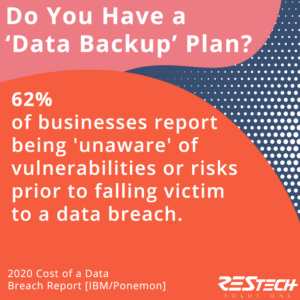
Have you heard Heraclitus’s quote, “The only constant in life is change”? There is nothing in life that can be predicted or expected with guaranteed certainty. This is not a mindboggling concept for most human beings, but some things can be planned for eventually. That is the most fundamental reason for your business to have a comprehensive backup plan in place now – so you are ready and protected for whatever the future may bring around. Don’t get caught unaware when you know that the odds are stacked against you.
Downtime and data loss events can cost a business large sums of money, especially if you do not have a comprehensive disaster recovery and business continuity strategy in place. Planning beyond just traditional data backups and including a robust data protection plan that factors in downtime disruptions and data corruption incidents can help mitigate or even prevent many of the most costly and frustrating events, so you can keep your organization running smoothly.
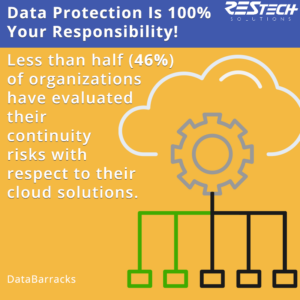
The cloud has been an incredible asset and game-changer for businesses of all sizes and industries. It enables and empowers growth, collaboration, and unprecedented access from any location or device at any time. Unfortunately, there are often a lot of assumptions or simple ignorance about who is responsible for securing or backing up the cloud applications and the data you entrust within these third-party systems. The most important truth you need to understand and make a priority is that when it comes to the cloud, protecting your data is totally and 100% your responsibility. Your SaaS vendors are not set up or designed to safeguard your data.
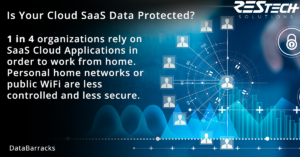
Remote work is only becoming more prevalent for businesses worldwide. Your remote workforce is increasingly reliant on Cloud Software-as-a-Service (SaaS) applications to carry out everyday operational functions. However, these decentralized home networks or public WiFi connections are lacking controlled security measures putting your data systems at even greater risk than normal, especially if you mistakenly believe your Cloud vendors are safeguarding your information assets. Your third-party cloud vendors are not responsible for protecting or retaining backup copies or recovery options for YOUR data! Be sure you include your SaaS application data in your backup and recovery strategies.
Ransomware continues to evolve and adapt to wreak havoc on businesses all over the world. Don’t assume that paying these criminal hackers the ransom will enable you to fully recover or restore your data – in fact, we are seeing more and more victims pay the ransom and still lose a portion, if not all, of their data and system assets. While it won’t prevent theft from a data breach, a comprehensive and multi-layer backup solution has been proven time and again to be a business saver when ransomware hits.
If the last year and a devastating global pandemic have taught us anything, it is that things can get worse. As if it wasn’t already growing and fruitful enough, cybercrime enterprise continues to reap exponential success on the coattails of the COVID-19 crisis. The entire world is now experiencing or has experienced the impacts of cyber warfare being persistently carried out by smart, skilled, and sophisticated criminals. With cyberattacks that result in total data loss skyrocketing over the last year, it’s never been more important to back up your data.
Can your business afford the cost of an entire week of downtime or disruption from a cyber attack like ransomware? Better yet, could it survive all the additional consequences and impacts of such an event? Analyzing the cost of a major downtime or data loss incident, like ransomware, in terms of smaller measurable blocks of time can help you visualize, understand and calculate just how costly and potentially damaging one of these attacks could be for YOUR organization. Protect your data and your business profits by implementing a layered backup solution today, and your return on investment could be priceless!
Cyber attacks are becoming increasingly complex and sophisticated, with many hackers aggressively targeting companies along their trusted supply chain. A comprehensive backup plan that includes disaster recovery and business continuity measures is one of the most important security defense tactics you can implement to protect your critical data and system integrity. Have you implemented a layered backup system to protect your business from cyber supply chain risks and threats?
As a proven security strategy against data loss and corruption threats, data backups are your best proactive prevention against data loss. Essentially, there really is no such thing as having too many backup copies. With new variants of ransomware evolving and adapting to circumvent traditional security measures and sophisticated deception tactics being aggressively deployed via your trusted supply chain vendors, don’t rely on hope and a wish. You must have a backup strategy that includes multiple points of failure to ensure you can recover from any type of data loss event.
Businesses around the globe are now seeing the next generation of cyberattacks aiming at open-source software communities. In fact, these attacks have quadrupled in the last year by over 430%! Be extra vigilant and cautious when working with these third-party channels, especially with trusted programmers and developers, as they are a HOT target for cybercriminals at present. By aggressively infiltrating at the top of such interconnected supply chain workflows, hackers can deploy successful attacks along with legitimate integrations and system updates.
Do you have a comprehensive backup strategy and solution that protects all your data assets, systems, and applications which facilitate and drive critical business operations?